A Cautionary Tale – The Importance of Layered Security Even in a P2PE Environment
A recent hacking attempt at a major credit card processor has driven some important conversations between our security experts and the IT departments of some of our key customers. It has resurrected the importance of security fundamentals in retail environments even if a P2PE (Point-to-Point Encryption) platform is in place as part of the POS system.
The hacker used an old Malware tool called Ordinaff C&C to re-direct P2PE transaction data traveling to the processor to an unsecured server in Curaco. The use of Ordinaff, which was originally designed to steal bank information and has a well-known malware signature, suggests that it was an inexperienced hacker who dug up an old tool to see what damage could be done.
However, it is possible that this was done by a pro, who re-purposed Ordinaff to try to pick-off credit card data flowing from merchants to the processor. In general, professional hackers aren’t out to use the credit card numbers that they capture themselves, but instead seek to sell them in bulk on the dark web. As such, it is easier to perform an attack like this, that collects data at an aggregation point, than hack into hundreds of individual merchant sites. Also, credit card processors recognize breaches by identifying a common point of purchase. This hacking approach would spread the point of purchase across a large number of merchants. If this was indeed a pro, it suggests that they thought they had the ability to de-crypt the data, possibly with an exposed encryption key.
It is yet another example of the continued efforts by hackers to find ways to work through barriers in order to steal and monetize transaction information. It also reinforces the importance of implementing a layered approach to security that includes a managed firewall, even if encryption is employed.
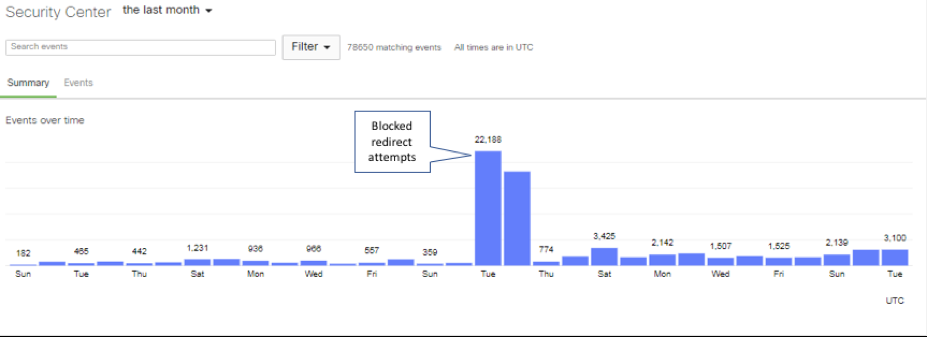
Our Security Operations Team was able to see our network of managed firewalls detect and block the attempts to route outbound traffic using invalid SSL certificates.
With the proliferation of data breaches and concerns about privacy and data use playing out in headlines and televised congressional hearings, IT security investment is more important than ever. Most IT professionals I know don’t want to have to explain to their executive management team how a lack of fundamental security elements put their company on the wrong side of the headlines.

About the Author:
Eric Weinkam
Vice President of Service Delivery at NuArx
Eric is a technical executive with over 20 years of experience in information technology; implementing organizational technology strategy, enterprise planning, and governance at the department or PMO Director level. He has hands-on experience with various project management methodologies including Agile/SCRUM.


